Kubernetes Integration
Connect Calmo to your Kubernetes clusters to enable comprehensive container orchestration, monitoring, and troubleshooting through AI assistance. This integration provides access to 15+ specialized tools across 5 categories for complete cluster management.Overview & Value Proposition
The Kubernetes integration transforms how your team manages containerized applications by providing:- Cluster-Wide Visibility - Monitor pods, services, deployments, and resources across namespaces
- Intelligent Troubleshooting - AI-powered analysis of pod failures, resource constraints, and configuration issues
- Safe Operations - Read-only tools enabled by default with granular control over write operations
- Multi-Cloud Support - Works with GKE, EKS, AKS, and self-managed clusters
- Context-Aware Management - Switch between clusters and namespaces seamlessly
Key Capabilities
When connected, Calmo gains access to 15+ Kubernetes tools across 5 categories:| Category | Tools | Capability |
|---|---|---|
| Resource Management | 5 tools | Get, list, describe, apply, and create Kubernetes resources |
| Operations | 4 tools | View logs, scale deployments, patch resources, manage rollouts |
| Cluster Management | 3 tools | Switch contexts, list API resources, explain resource types |
| Advanced Operations | 3 tools | Port forwarding, resource deletion, generic kubectl commands |
| Helm Operations | 3 tools | Install, upgrade, and uninstall Helm charts |
Prerequisites
- Kubernetes cluster access (GKE, EKS, AKS, or self-managed)
- Valid kubeconfig file with appropriate permissions
- For cloud providers: Service account keys (optional but recommended)
- Calmo account with team or personal workspace
Setup Methods
Method 1: Kubeconfig Upload (Recommended)
Step 1: Prepare Your Kubeconfig- Locate your kubeconfig file (typically
~/.kube/config) - Ensure it contains valid cluster credentials and contexts
- Verify access by running:
kubectl cluster-info
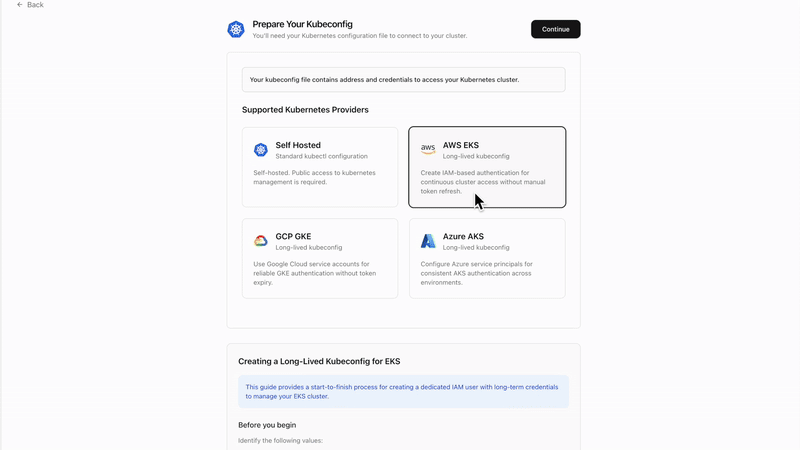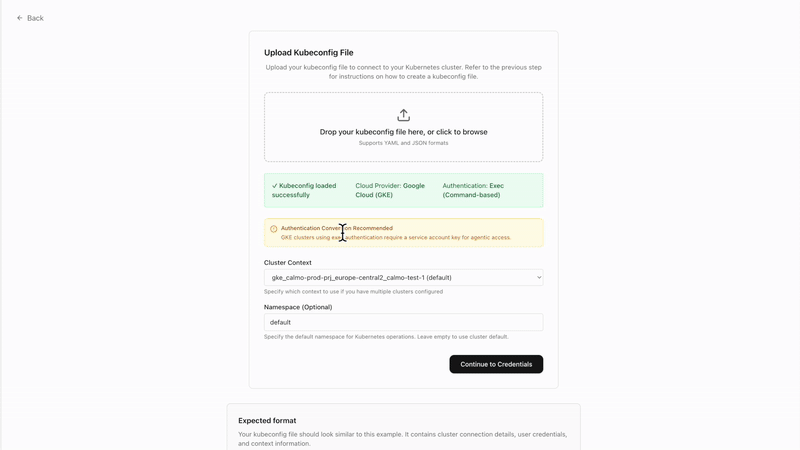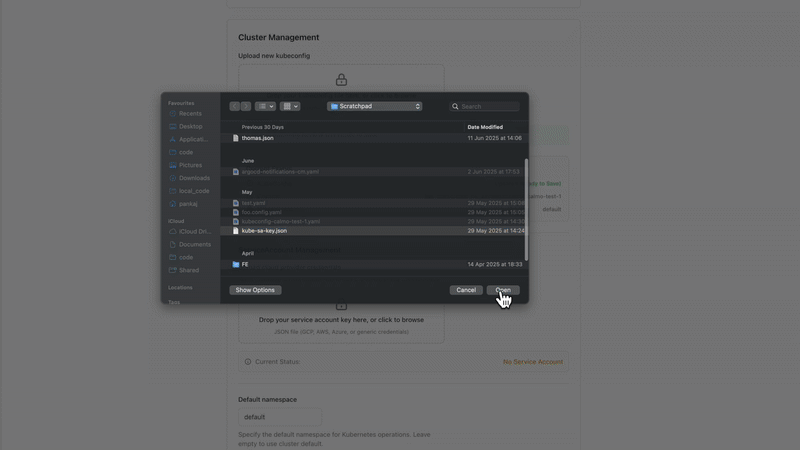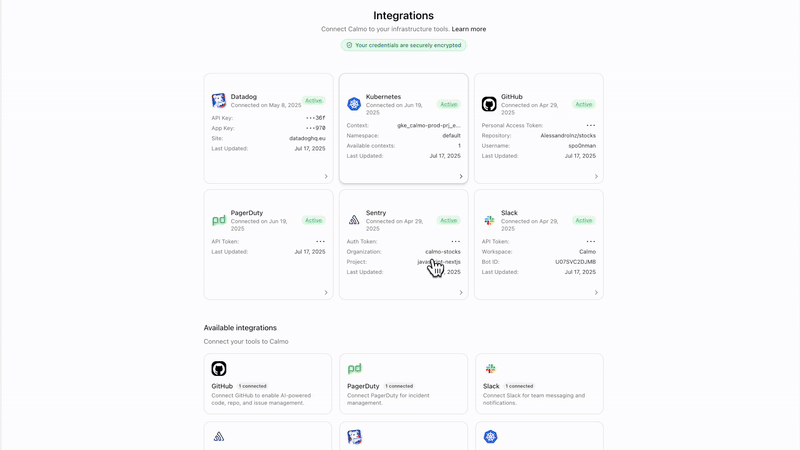
- Navigate to Integrations in your Calmo dashboard
- Click Kubernetes integration
- Choose Upload Kubeconfig File
- Select your kubeconfig file or paste the contents
- Select your desired context from available options
- Choose target namespace (default:
default)
Method 2: Cloud Provider Service Account (Enhanced Security)
For enhanced security with cloud providers, you can supplement kubeconfig with service account keys:Google Kubernetes Engine (GKE)
- Create a service account in Google Cloud Console
- Assign appropriate Kubernetes permissions
- Download the service account key (JSON)
- Upload both kubeconfig and service account key to Calmo
Amazon Elastic Kubernetes Service (EKS)
- Configure AWS IAM role with EKS permissions
- Update kubeconfig with AWS authentication
- Provide AWS credentials through service account key
Azure Kubernetes Service (AKS)
- Create Azure service principal
- Assign Kubernetes permissions
- Configure kubeconfig with Azure authentication
⚙️ Operations (Mixed Safety)
Default: Logs only - Operational tasks with varying risk levels- kubectl_logs - View container logs (✅ Read-only)
- kubectl_scale - Scale deployments (⚠️ Write operation)
- kubectl_patch - Patch resource configurations (⚠️ Write operation)
- kubectl_rollout - Manage deployment rollouts (⚠️ Write operation)
🗂️ Cluster Management (Read-Safe)
Default: Enabled - Essential cluster navigation- kubectl_context - Switch between cluster contexts
- list_api_resources - Discover available Kubernetes APIs
- explain_resource - Get resource documentation and schemas
🔧 Advanced Operations (High Risk)
Default: Disabled - Powerful but potentially dangerous operations- port_forward - Forward local ports to pods (⚠️ Network access)
- kubectl_delete - Delete Kubernetes resources (⚠️ Destructive)
- kubectl_generic - Execute arbitrary kubectl commands (⚠️ Unrestricted)
📦 Helm Operations (Package Management)
Default: Disabled - Helm chart lifecycle management- install_helm_chart - Install Helm charts (⚠️ Write operation)
- upgrade_helm_chart - Upgrade existing releases (⚠️ Write operation)
- uninstall_helm_chart - Remove Helm releases (⚠️ Destructive)
Team vs Personal Configuration
Team/Organization Setup
- Shared cluster access across team members
- Centralized tool configuration and policies
- Organization-level context and namespace defaults
- Team administrators can manage tool permissions
Personal Setup
- Individual cluster connections
- Personal tool preferences and configurations
- Private contexts and namespace selections
- Full control over enabled capabilities
Security & Best Practices
⚠️ Safety Recommendations
- Start with Read-Only - Enable only read operations initially
- Gradual Enablement - Add write operations as trust builds
- Namespace Isolation - Restrict to specific namespaces when possible
- Regular Auditing - Review enabled tools and permissions periodically
- Service Account Keys - Use cloud provider service accounts for enhanced security
🔒 Permission Levels
| Risk Level | Operations | Recommendation |
|---|---|---|
| Low | Get, List, Describe, Logs | ✅ Safe to enable |
| Medium | Apply, Create, Scale, Patch | ⚠️ Enable with caution |
| High | Delete, Generic commands | ❌ Enable only when necessary |
Configuration Management
Configure Tool Access**
Review and customize tool categories based on your needs:- ✅ Resource Management - Read operations (get, list, describe) enabled by default
- ❌ Write Operations - Apply, create, delete disabled by default for safety
- ✅ Cluster Management - Context switching and resource discovery enabled
- ❌ Advanced Operations - Port forwarding and generic commands disabled by default
Tool Categories & Configuration
🔍 Resource Management (Read-Safe)
Default: Enabled - Essential for cluster visibility- kubectl_get - Retrieve specific Kubernetes resources
- kubectl_list - List resources by type across namespaces
- kubectl_describe - Get detailed resource information
- kubectl_apply - Apply configuration changes (⚠️ Write operation)
- kubectl_create - Create new resources (⚠️ Write operation)
Updating Cluster Configuration
- Navigate to Integrations → Kubernetes
- Click Edit Configuration
- Upload new kubeconfig or service account keys
- Modify context and namespace selections
- Adjust tool permissions as needed
- Save changes
Managing Multiple Clusters
- Not yet supported
Troubleshooting
Common Issues
Connection Failed- Verify kubeconfig has valid credentials
- Check cluster connectivity:
kubectl cluster-info - Ensure proper context is selected
- Verify service account has required Kubernetes permissions
- Check RBAC policies in your cluster
- Ensure namespace access is properly configured
- Review enabled tool permissions
- Check if operations require write access
- Verify cluster resources exist and are accessible
Getting Help
- Reconnect Integration - Use the reconnect option in integration settings
- Update Credentials - Upload fresh kubeconfig or service account keys
- Contact Support - Reach out to [email protected] for assistance
Advanced Features
Multi-Cloud Support
- Google GKE - Full integration with Google Cloud service accounts
- Amazon EKS - AWS IAM integration for enhanced security
- Azure AKS - Azure Active Directory integration
- Self-Managed - Support for any standard Kubernetes cluster
Context & Namespace Management
- Switch between multiple cluster contexts
- Set default namespaces per context
- Maintain separate configurations per environment
- Support for namespace-scoped operations
For additional help with Kubernetes integration, contact our support team at [email protected].
